Topic: How to configure the vicibox 10 dynamic portal with dynamic ip list.
Challenge :
The Recent release of Vicibox10 (ViciBox_v10.x86_64-10.0.0.iso ), have some bugs with respect to dynamic portal for dynamic ip list and public zone.
BUG's/Issues
1. Dynamic IP's getting added in blackips IPSET list.
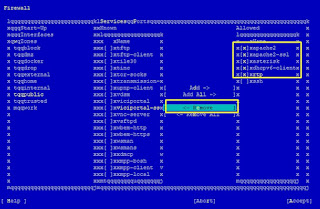
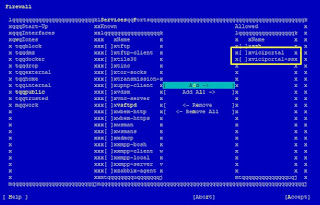
2. IPSet Public Zone missing the rules for all List like whiteips,whitenets,dynamic clist for the services like asterisk,apache2,apache2-ssl
Overview:
In this blog i will be covering both the bug fix and configuration steps for the vicibox 10 dynamic portal with whitelist,dynamic ip list.
VICIdial is an enterprise class, open source, contact center suite in use by many large call centers around the world. VICIdial has a full featured predictive dialer. It is capable of inbound, outbound, and blended phone call handling.
VICIbox Server is the official installation CD for the VICIDIAL Call Center Suite. It is based off of OpenSuSE server, and will properly install the VICIDIAL Call Center Suite with relative ease.
The ViciBox-Firewall is an integration of the underlying firewall in the OS, various features of ViciDial, and some add-on ViciBox features. This allows for the relatively easy administration of all network access to the various features of ViciDial. The firewall integration itself supports a Black list, a White list, a Dynamic List with a user authentication portal
Firewalld/IPSET/Nftable
Vicibox 10 Dynamic Portal use three major components
1. IPSET
2. nftables
3. Firewalld
ipset is a companion application for the iptables Linux firewall. It allows you to setup rules to quickly and easily block a set of IP addresses, among other things.
nftables is a Linux packet classification framework that replaces the Netfilter infrastructure behind iptables, ip6tables, arptables, and ebtables ,
firewalld is a zone-based firewall. Zone-based firewalls are network security systems that monitor traffic and take actions based on a set of defined rules applied against incoming/outgoing packets.
it is better to have knowledge in these components ,which helps in troubleshooting and understand how vicibox dynamic portal works, click on the hyperlinks for more details.
Youtube Link for the video tutorial click here
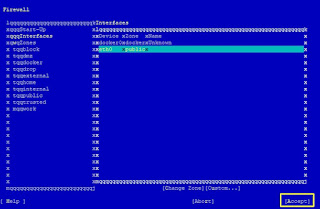
STEP 1: Bug fix the VB-firewall code.
SSH to the server, Edit the VB-firewall and replace IPBLACK to IPDYNAMIC at line no 763
vi +763 /usr/bin/VB-firewall
doipnetslist(\@dynamicips, $IPBLACK, "X", "DynamicList");
to
doipnetslist(\@dynamicips, $IPDYNAMIC, "X", "DynamicList");
or run the below command to replace the word IPBLACK to IPDYNAMIC
cd /usr/bin/
sed -i '763s/IPBLACK/IPDYNAMIC/' VB-firewall
<rule family="ipv4"><source ipset="whiteips"/><service name="apache2"/><accept/></rule><rule family="ipv4"><source ipset="whitenets"/><service name="apache2"/><accept/></rule><rule family="ipv4"><source ipset="dynamiclist"/><service name="apache2"/><accept/></rule><rule family="ipv4"><source ipset="whiteips"/><service name="apache2-ssl"/><accept/></rule><rule family="ipv4"><source ipset="whitenets"/><service name="apache2-ssl"/><accept/></rule><rule family="ipv4"><source ipset="dynamiclist"/><service name="apache2-ssl"/><accept/></rule><rule family="ipv4"><source ipset="whiteips"/><service name="asterisk"/><accept/></rule><rule family="ipv4"><source ipset="whitenets"/><service name="asterisk"/><accept/></rule><rule family="ipv4"><source ipset="dynamiclist"/><service name="asterisk"/><accept/></rule></zone>
@reboot /usr/bin/VB-firewall --voipbl --noblack --quiet0 */6 * * * /usr/bin/VB-firewall --voipbl --noblack --flush --quiet
@reboot /usr/bin/VB-firewall --white --dynamic --quiet* * * * * /usr/bin/VB-firewall --white --dynamic --quiet
Finaly give reboot to the server
type reboot.
firewall-cmd --list-all - to check services and rules in public zone
nft list table inet firewalld - list the nftables rules.